TOR. dot Onion. Hidden Services. Dark Net. Dark Web. OpSec. Anonymity. We’ve all heard of these. But what are they? Who runs them? How do they work? Let’s demystify this stuff, step by step, and set up our own legit Hidden Service.
– Table of Contents
– why (is any of this necessary)
– how to set up your hidden service. Linux only (this is why you’re here, tho’, TLDR; hit this)
– my example hidden service. Relax, it’s legit. Nothing even questionable is going on.
A word on Anonymity, Privacy, OPerational SECurity online:
Anonymity is one of the basic principles of the Internet. Just like when you’re away from the keyboard, it is a concept that allows one to not disclose their identity in certain interactions.
Privacy is what most people consider an inalienable right, be it online or in the offline world. Some people are surprisingly ignorant enough about this right, that they freely give it up without even thinking twice. But hypocritically, they are very selective about which privacy right applications they are concerned: they’ll say they don’t care about privacy in exchange for a little extra perceived security (which is almost never the case), however they still lock their doors and pull down their curtains where they live. We can’t have it both ways.
Some others have said it far more eloquently than I ever could:
"Arguing that you don't care about the right to privacy because you have nothing to hide, is no different than saying you don't care about free speech because you have nothing to say."Edward Snowden
OPerational SECurity is the concept that no matter how much technology one employs to stay safe and secure from prying eyes, it’s all useless if they don’t also modify their behavior to match the security, anonymity and privacy of their technical tool set.
Most often it’s the human element with bad behavior that lifts the protection conferred by technology.
It’s a concept to take to heart because everyone benefits from tighter OPSEC, not just people with something to hide.
Now, let’s get to it…
– what is TOR
It stands for The Onion Router, a suite of tools to protect online anonymity and privacy, including a specially configured browser based on Mozilla Firefox, a network routing mechanism to route web requests, a proxy for other, non HTTP applications, and so on; all neatly packaged together under the TOR name.
Most folks know about the browser, because that’s what they interact with. Not everyone needs to know how it all works under the hood. And for brevity purposes, we’re not getting too deep into that either.
It is very important to a lot of people, some with valid, legitimate needs to exercise these rights on a daily basis; like people living under oppressive regimes, political dissidents, journalists and watchdog organizations, scientists, infosec professionals, and even government actors.
– what are Hidden Services, or onions (in this context)
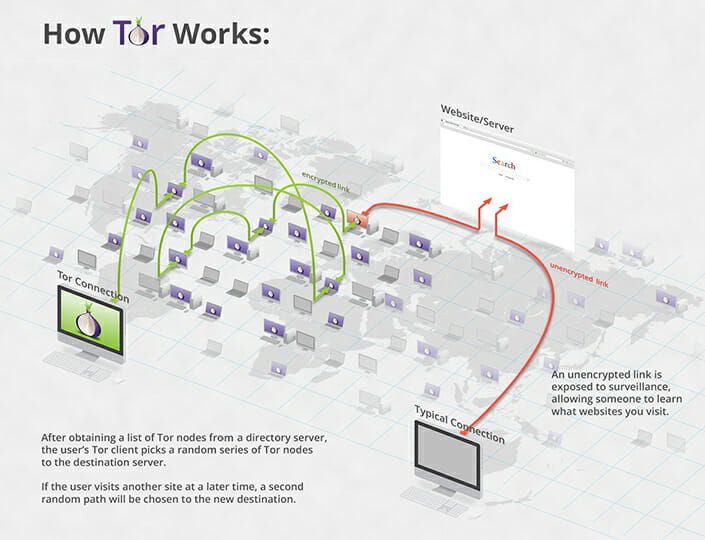
Onions, or Hidden Services, are websites, or rather, hidden web addresses that are only accessible via the TOR Browser. Because of the way the TOR Network operates, the traffic from your computer to any .onion address will have ‘jumped’ through 3 other nodes on the TOR Network, before reaching its final destination. And all hops are encrypted and anonymized from each other.
This happens for each different site/address that you request, be it with an .onion suffix or a traditional .com, .net, .whatever (those on the ‘clearnet’).
– why is any of this necessary
There are way too many reasons to list, in favor of striving to maintain some level of anonymity and privacy online. But the few more notable ones include pervasive blanket surveillance by various entities, like major governments. Or organized crime successfully stealing identities for further nefarious purposes. Or legit companies being digitally attacked by other companies, ‘hackers for hire’ and foreign state actors, leading to industrial espionage of trade secrets and other sensitive information. And the list goes on and on and on.
– how to set up a Hidden Service
Or the main meat of why I even bothered to lay this out at all.
This only covers how to set it up either on your laptop/desktop, or preferably an online server somewhere, that you own/pay for.
Disclaimer: Although this tutorial only illustrates how to set up a completely legal, valid and legitimate service on the TOR Network, be sure that you are not breaking any law or even terms of service or any agreement you may have signed with your hosting or internet service provider. Go read the agreements you’ve accepted when you’ve signed up.
First, the assumptions/requirements:
– linux box, running an up to date Debian derivative; I’m running Ubuntu. Must have root access. It’s extremely similar and trivial to set this up on any other Linux distribution.
– able to run TOR package on there, in no breach of any terms of service with any entity.
1. install the tor package on your machine:
sudo apt update; sudo apt install tor
2. edit your torrc file, modify the Dir and Port
Typically in /etc/tor/torrc and look for #HiddenServiceDir. Un-comment that line by removing the hashtag character from it. I prefer using vimas my editor, so
sudo vim /etc/tor/torrc
In the same torrc file, the very next line is #HiddenServicePort.
Uncomment this one as well, the same way, by removing the hashtag sign from it. At the end of this line, append 80. Now save the file.
So far, the two lines should now look like so:
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:8080
And restart TOR via:
sudo /etc/init.d/tor restart
If all is well, you should see something like so:
[ ok ] Restarting tor (via systemctl): tor.service.
Also, double check that all is well by issuing this command:
sudo netstat -tulpen | grep -i tor
If the TOR process is working, it’ll show as it’s listening on localhost on port 9050:
tcp 0 0 127.0.0.1:9050 0.0.0.0:* LISTEN 0 54791 3097/tor
3. If all went well, then great news, you have successfully generated a NAME for your site. It’s random, by default.
There is a way to obtain some vanity URLs if you have enough computing power, but it’s not necessary.
So, the name. There is a .onion file that just got generated for you upon restarting TOR. It lives, based on this example, and assumptions above, at: /var/lib/tor/hidden_service/hostname
Pull that file up:
cat /var/lib/tor/hidden_service/hostname
That, for me, yields: 27nhctqiapgxkpr5h7r52t5l5oh4ajphttswy6hrdsjybllnr5cqsnqd.onion
If all is not well, then look at the TOR startup log. Typically it doesn’t like the directory path we’ve seen earlier, or it doesn’t have enough permissions to write to that path, or I often have seen it say that the directory permissions are too.. permissive. For the directory it needs to read, write and traverse, for the files it needs read and write permissions. Group and other don’t need permissions on that path.
4. install a webserver. I’m quite partial to nginx:
sudo apt install nginx
5. edit the configuration of this webserver
In /etc/nginx/sites-enabled/default. Find the ‘listen’ directive. Modify that from whatever it is, into:listen *:8080;
Now, inside the same server block ( server { ), find the root directive. Make sure it points at some directory you’d like, typically under /var/www. Mine looks like:root /var/www/my_awesome_hidden_service;
Also make sure the server_name directive is the onion address you’ve previously uncovered from the /var/lib/tor/hidden_service/hostnamecontents, at step 3. That ‘3uw6ipkk64532szg.onion‘ in my case. Yours will be different, of course. That line, in my nginx server file looks like so: server_name 3uw6ipkk64532szg.onion; Again, yours will be different, probably longer, but still ending in .onion
6. create that directory from the previous step, as it most likely doesn’t exist. I did:
mkdir -p /var/www/my_awesome_hidden_service
Create an index.html file in there with something, like “hello”:
echo "hello hidden service" > /var/www/my_awesome_hidden_service/index.html
Save it.
Test nginx configuration by issuing this command:
sudo nginx -t
If you don’t see:
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
fix whatever minor typo you may have and test again until you see the two lines above.
If all went well, you’d see the output confirming the configuration is ok. Therefore, restart nginx:
sudo service nginx restart
After that, open TOR Browser this time, on your computer, and navigate to your known .onion. Enjoy!
Congratulations! ♥
And if you get stuck, leave a comment with whatever error message of any of the commands you see, or whatever question you might have, and I’ll get back to you.
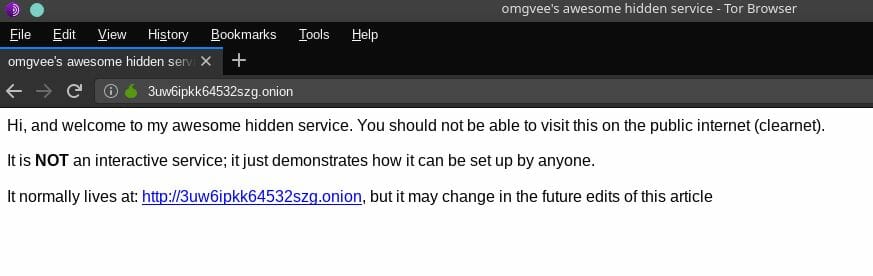
– my onion service is a simple static page…
That means that you can see this hidden service anonymously, over the TOR Network, by going to:
27nhctqiapgxkpr5h7r52t5l5oh4ajphttswy6hrdsjybllnr5cqsnqd.onion
Here it is, in “action”… though it’s pretty static.